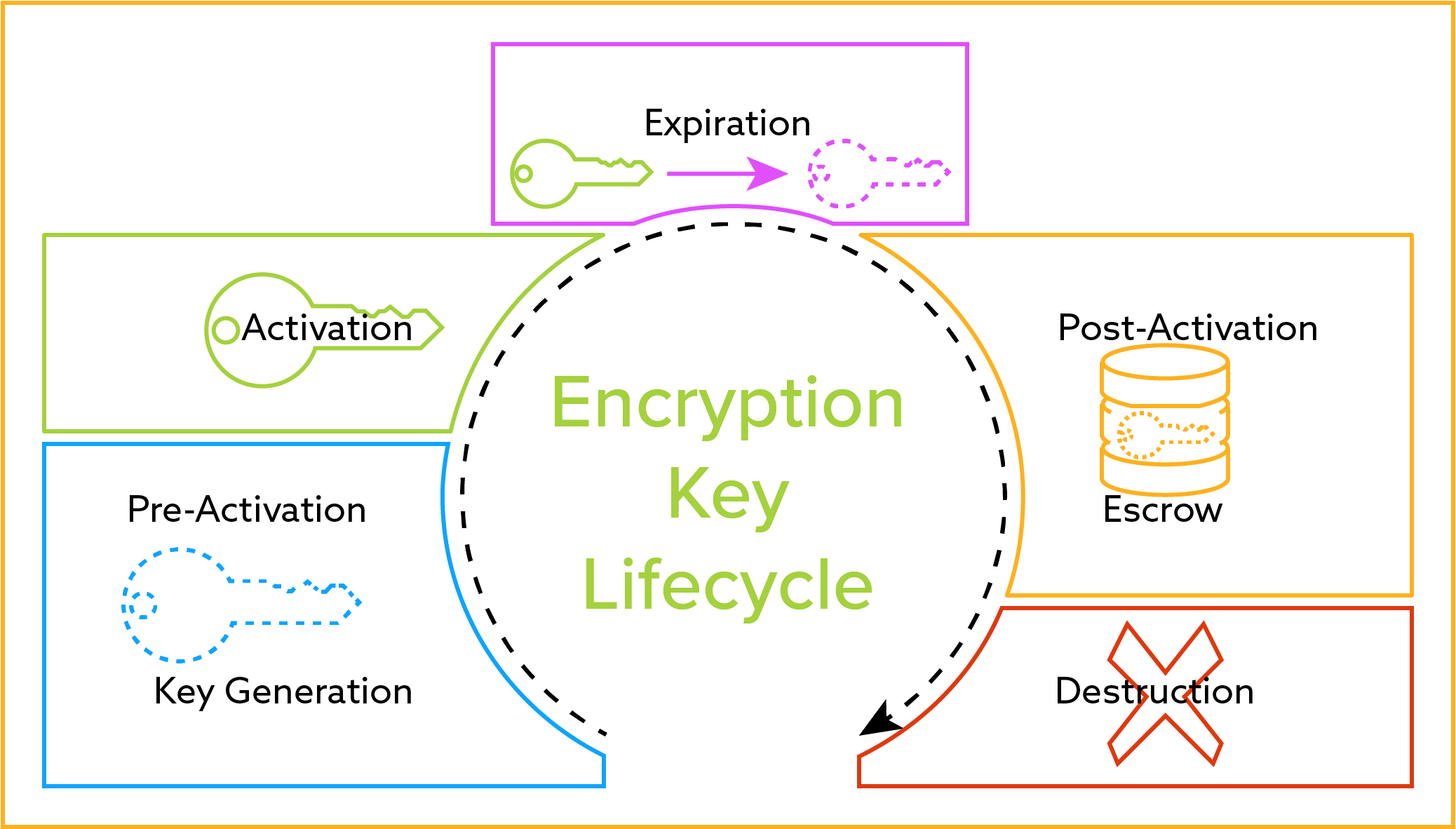
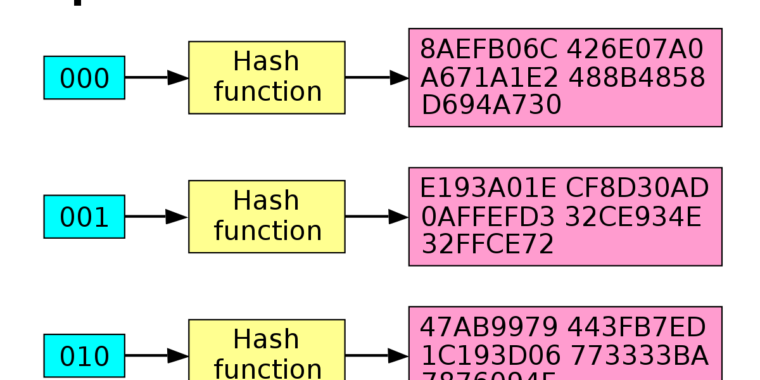
Keys Algorithm Among Us
Keys algorithm among us. Among Us Game lately is being an extremly by popular games, maybe it is because it is very addictive game to play. Become an impostor are the dream by player in Keys algorithm among us game. Because you can toy your friend and It is funny to watch friends fighting among others to vote for the impostor, and sometimes they are of to argue who is Is the real Impostor Keys Algorithm Among Us.
Incoming Search Terms:
- The Definitive Guide To Encryption Key Management Fundamentals Keys Algorithm Among Us,
- Among Us Crewmate Guide 5 Tips To Outsmart The Imposter Keys Algorithm Among Us,
- 3 Keys Algorithm Among Us,
- Quantum Computing And The End Of Encryption Hackaday Keys Algorithm Among Us,
- Among Us Pc Game Hotkeys Defkey Keys Algorithm Among Us,
- Http Www Di Ens Fr Pointche Documents Papers 2007 Pairing Pdf Keys Algorithm Among Us,
More From Keys Algorithm Among Us
- Purple Mini Crewmate Sitting
- Picture Of A Among Us Character
- Text Art Copy And Paste Among Us
- Purple Among Us App
- Skin Unlocker Among Us Android
If you re looking for download Skin Unlocker Among Us Android you've come to the right location. We have 104 download source about skin unlocker among us android adding apk, cheat, cheat apk, wallpapers, and more. In these web page, we also provide number of apk out there. Such as png, jpg, animated gifs, pic art, logo, blackandwhite, translucent, etc.